- Fingerprint Books
- Fingerprint Equipment
- Fingerprint News
- Fingerprint Research
- Fingerprint Videos
- Crime Scene Equipment
- Crime Scene News
- Crime Scene Research
- Crime Scene Videos
- Court Testimony News
- Case Studies

New Powder Suspension Formula for Fingerprint Development on the Adhesive Side of Tape
Are detectives discounting the associative value of fingerprints that fall short of an identification in their investigations, using the ncic bayesian network to improve your afis searches, dna decontamination of fingerprint brushes, accuracy and reproducibility of conclusions by forensic bloodstain pattern analysts, non destructive dna recovery from handwritten documents using a dry vacuum technique, simulating dead bodies could help calculate an accurate time of death, trees and shrubs might reveal the location of decomposing bodies, presenting fingerprint comparisons in court using forensic comparison software, assessing the reliability of a clothing-based forensic identification, u.s. justice department issues draft guidance regarding expert testimony and lab reports in forensic science, how making a murderer will change the way we think about justice, zodiac killer code cracked by australian mathematician samuel blake more than 50 years after first murder, when a dna test says you’re a younger man, who lives 5,000 miles away, you could be your cat’s favorite meal, claremont serial killings trial told ciara glennon fingernail dna find proved a major ‘turning point’, the 25 best true-crime documentaries on netflix.

Scientists identify gases unique to rotting pigs and human bones
‘forensic breakthrough’ leads to potential suspect in 40-year-old irish massacre, the quantum mechanics of fingerprints on your water glass, bacteria on shoes could help forensic teams catch suspects.
Ted Bundy Although serial killer Ted Bundy was responsible for an estimated 30-plus murders, there was little physical evidence to connect him to the crimes when he was arrested in 1975. Two years later, having been convicted only of kidnapping, Bundy was preparing to stand trial for murder in Colorado when he escaped and headed to Florida. There, he killed three more people early in 1978, and when he was finally captured in February of that year, the physical evidence in those cases led to his conviction. Most crucial was the matching of a bite mark on the buttock of victim Lisa Levy to the Bundy’s distinctive, crooked and chipped teeth. He was convicted also of the murder of 12-year-old Kimberly Leach based on fibres found in his van that matched the girl’s clothing. Bundy was put to death in 1989.

The Lindbergh Kidnapping On March 1, 1932, Charles Lindbergh Jr., the 20-month-old son of the famous aviator, was kidnapped, and although a ransom of $50,000 was paid, the child was never returned. His body was discovered in May just a few miles from his home. Tracking the circulation of the bills used in the ransom payment, authorities were led to Bruno Hauptmann, who was found with over $14,000 of the money in his garage. While Hauptmann claimed that the money belonged to a friend, key testimony from handwriting analysts matched his writing to that on the ransom notes . Additional forensic research connected the wood in Hauptmann’s attic to the wood used in the make-shift ladder that the kidnappers built to reach the child’s bedroom window. Hauptmann was convicted and executed in 1936.

The Atlanta Child Murders In a two year period between 1979 and 1981, 29 people — almost all children — were strangled by a serial killer. Police staked out a local river where other bodies had been dumped and arrested Wayne Williams as he was driving away from the sound of a splash in an area where a body was recovered a couple of days later. Police didn’t witness him drop the body, so their case was based largely on forensic evidence gathered from fibers found on the victims . In all, there were nearly 30 types of fiber linked to items from Williams’ house, his vehicles and even his dog. In 1982, he was convicted of killing two adult victims and sentenced to life in prison, although the Atlanta police announced that Williams was responsible for at least 22 of the child murders.

The Howard Hughes Hoax In 1970, authors Clifford Irving and Richard Suskind concocted a scheme to forge an autobiography of notoriously eccentric and reclusive billionaire Howard Hughes. Assuming that Hughes would never come out from hiding to denounce the book, they felt that their plan was fool-proof. Irving went to publisher McGraw-Hill claiming that Hughes had approached him to write his life story and that he was willing to correspond with only the author. As proof, Irving produced forged letters that he claimed were from Hughes. McGraw-Hill agreed, paying $765,000 for the right to publish the book. When word of the book was made public, however, Hughes contacted reporters to denounce it as false. Not wishing to appear in public, the billionaire would talk to reporters only via telephone. Thus, a “spectographic voiceprint analysis,” measuring tone, pitch and volume, was conducted to determine if the speaker was indeed Howard Hughes. Although a handwriting expert had previously been fooled by the notes that Irving had forged, the voice analyst correctly identified the speaker as Hughes. Irving was exposed and confessed before the book was published. He spent 17 months in prison, while Suskind spent five. Irving later wrote a book about the scheme, The Hoax , which became a major motion picture in 2008.

The Night Stalker Between June 1984 and August 1985, a Southern California serial killer dubbed the Night Stalker broke into victims’ houses as they slept and attacked, murdering 13 and assaulting numerous others. With citizens on high alert, an observant teenager noticed a suspicious vehicle driving through his neighborhood on the night of August 24, 1985. He wrote down the license plate and notified police. It just so happened that the Night Stalker’s latest attack took place that night in that area, so police tracked down the car. It had been abandoned, but police found a key piece of evidence inside: a fingerprint . Using new computer system, investigators quickly matched the print to 25-year-old Richard Ramirez and plastered his image in the media. Within a week, Ramirez was recognized and captured by local citizens. He was sentenced to death.

Machine Gun Kelly George “Machine Gun” Kelly was a notorious criminal during the Prohibition era, taking part in bootlegging, kidnapping and armed robbery. On July 22, 1933, he and another man kidnapped wealthy Oklahoma City oilman Charles Urschel. After a series of ransom notes and communications, a $200,000 ransom was paid — the largest amount ever paid in a kidnapping to date. Urschel was released nine days later, unharmed. The oilman had shrewdly paid close attention to every detail during his ordeal and was able to relate it all to police. Although he was blindfolded, he could tell day from night and was able to estimate the time of day that he heard airplanes fly above. He also noted the date and time of a thunderstorm and the types of animals he heard in what he presumed to be a farmhouse. Using his memories, the FBI pinpointed the likely location in which Urschel was held to a farm owned by Kelly’s father-in-law. What truly linked Kelly and his gang to the kidnapping, though, was Urschel’s fingerprints , which he made sure to place on as many items in the house as possible. Kelly was sentenced to life in prison, where he died in 1954.

The Green River Killer The Green River Killer was responsible for a rash of murders — at least 48 but possibly close to 90 — along the Green River in Washington state in the ’80s and ’90s. Most of the killings occurred in 1982-83, and the victims were almost all prostitutes. One of the suspects that police had identified as early as 1983 was Gary Ridgway , a man with a history of frequenting and abusing prostitutes. However, although they collected DNA samples from Ridgway in 1987, the technology available didn’t allow them to connect him to the killings. It wasn’t until 2001 that new DNA techniques spurred the reexamination of evidence that incriminated Ridgway . He was arrested and later confessed. Ridgway pleaded guilty to 48 murders — later confessing to even more, which remain unconfirmed — in exchange for being spared the death penalty. He was sentenced to 48 life sentences without the possibility of parole.

BTK Killer The BTK (“Bind, Torture, Kill”) Killer was a serial killer who terrorized the Wichita, Kansas area between 1974 and 1991, murdering 10 people over the span. The killer craved media attention and sent letters to local newspapers and TV stations, taunting investigators. It’s this egotism that led to his capture, however. When he resurfaced in 2004 with a series of communications, he chose to send a computer floppy disk to the Wichita Eagle . Forensic analysts traced the deleted data on the disk to a man named Dennis at the Christ Lutheran Church in Wichita . It didn’t take long for the police to arrest Dennis Rader , who confessed and was sentenced to nine life terms in prison.

Jeffrey MacDonald Early in the morning of February 17, 1970, the family of Army doctor Jeffrey MacDonald was attacked, leaving the doctor’s pregnant wife and two young daughters dead from multiple stab wounds. MacDonald himself was injured by what he claimed to be four suspects, but he survived with only minor wounds. Doubt was immediately cast on the doctor’s story, based on the physical evidence on the scene that suggested that he was the killer. However, the Army dropped the case because of the poor quality of the investigative techniques. Several years later, though, MacDonald was brought to trial in a civilian court. Key evidence was provided by a forensic scientist who testified that the doctor’s pajama top, which he claimed to have used to ward off the killers, had 48 smooth, clean holes — too smooth for such a volatile attack. Furthermore, the scientist noted that if the top was folded, the 48 holes could easily have been created by 21 thrusts — the exact number of times that MacDonald’s wife had been stabbed. The holes even matched the pattern of her wounds, suggesting that the pajama top had been laid on her before during the stabbing and not used in self-defense by the doctor. This crime scene reconstruction was crucial in MacDonald’s conviction in 1979. He was sentenced to life in prison for the three murders.

John Joubert In 1983, two murders of schoolboys rocked the Omaha, Nebraska area. The body of one of the boys was found tied with a type of rope that investigators couldn’t identify. While following up on the lead of a mysterious man scouting out a school, they traced the suspect’s license plate to John Joubert , a radar technician at the local Air Force base. In his belongings, they found a rope matching the unusual one used in the murder (which turned out to be Korean). Although DNA analysis technology was not yet an option, the extreme rarity of the rope was enough to lead to Joubert’s confession . Furthermore, hair from one of the victims was found in Joubert’s car . The child killer was even linked to a third murder, in Maine, when his teeth were found to match bite marks on a boy killed in 1982. Joubert was found guilty of all three murders and was put to death in the electric chair in 1996.

Source: Criminal Justice School
- Serial Killers

More articles
[…] are perhaps the most well-known of the expert witness cadres, largely thanks to their importance in many high profile criminal cases. Forensics, generally speaking, is the use of scientific methods to aid in the solving of a crime. […]
LEAVE A REPLY Cancel reply
Log in to leave a comment

Latest article
Latest posts, popular posts, the acid test: can you dissolve a body completely, people about to commit a crime shouldn’t throw stones… why because we can get good fingerprints off them, crime scene chemistry – luminol, blood & horseradish, popular category.
- Case Studies & Stories 162
- Fingerprint News 59
- Fingerprints 45
- Crime Scene News 34
- Fingerprint Research 28
- Court Testimony News 27
- Crime Scene Research 20

Integrated Digital Forensic Laboratory Solutions
Efficient video forensic tool for recovering deleted, lost, or fragmented videos and perform rapid and effective forensics.
Aims to resolve the problems of deleted /corrupted/fragmented database files, false file systems, and restriction of application system accessibility.
All-in-one forensic data recovery tool helps you acquire and recover data from both good and damaged storage media like HDD easily.
Efficient phone forensic tool for extracting, recovering, analyzing data, and exporting data reports from various mobile devices.
- Law Enforcement
- Military & Intelligence
- IT & Finance
- Lab Constructor
- Professional Service
- Handy Solution
- Achievement
Write a Forensic Report Step by Step [Examples Inside]

To present the evidence in a way the court deems admissible and bring the guilty to justice, formulating a coherent and comprehensive digital forensics report is crucial. Without one, retelling the events that occurred in a structured manner, all while backing up every claim with concrete evidence, would be next to impossible (hence they are a requirement in the court proceedings).
Digital forensics reports play an instrumental role in coordinating the work between multiple investigators, law enforcement officers, administrative, and legal personnel involved in the case, not all of which may share the same professional background and field of expertise.
They are the interdisciplinary focal point that tells the truth of what happened and documents the findings, all while presenting them in a factual yet understandable manner.
At the same time, investigators should keep in mind that other law enforcement institutions may ask for the report in order to:
- Get a recap of events
- Determine the next steps to take
- Review the evidence
- Verify what digital forensics tools have been used
- Get an overview of the investigation’s objectives
Before we reveal the exact steps on how to formulate one, keep in mind that the exact structure of a digital forensic report depends on the case, which means what you will find below is a general overview of the entire process in a step-by-step manner as well as a general outline to follow which should give you some ideas on how to tackle the task at hand.
To give you a better idea how the final result should look, we’ve also provided some concrete digital forensic report examples from different cases.
With that out of the way, let’s begin with :
STEP 1: Familiarize Yourself with the Best Practices of Writing a Digital Forensic Report
Step 2: study some generic and recommended forensic report examples before writing, step 3: write the digital forensics report, step 4: re-check your report for factual correctness and apply edits as needed, step 5: present the report to the court, digital forensic lab can help you automate your reporting.

Before you begin with the writing process, it’s a good idea to familiarize yourself with the most important principles to keep in mind the entire time.
These can be summarized as follows:
Don’t break the law when collecting, processing, analyzing, or handling evidence
No law enforcement officer or digital forensics investigator is above the law, so everyone’s rights need to be respected during the entirety of the investigation. The forensic report you present needs to make this clear beyond any doubt, so you should state any warrants you’ve obtained to search and confiscate a device, etc.
Only mention the information that’s relevant
Just think of it like telling a story. If it fails to captivate the reader’s attention, there is a risk the reader will put it down before getting to the end.
The purpose of a digital forensics report is to help the reader connect the dots and lead them on a journey of discovery.
Focus on concrete facts rather than your personal opinions
When trying to get someone to answer for their deeds and convict them in court, you’re going to need more than just a subjective opinion, so focus on stating concrete evidence and facts.
Remember that anyone can argue with someone’s opinion, but facts are indisputable.
Utilize any forensics notes you’ve made during the investigation itself
Did your work begin with suspicion or a clue you started investigating? This can add value and enrich the section where you talk about the stages of the investigation and how you came to your conclusions.
If a particular part of the digital forensics process was especially challenging, shed some light on why that was the case and how you managed to overcome these challenges.
Avoid using complex terms and focus on conveying the relevant information in a manner that is coherent and simple to understand
The reason being is that not everyone who will read the report has the same professional background as you.
During the investigation and legal proceedings, expect to be working with IT professionals, legal professionals, and law enforcement personnel who all need to be kept on the same page. Of course, you shouldn’t strip out all of the industry terms such as IP addresses, timestamps, hash values, and similar, all of which can be crucial pieces of evidence.
However, when mentioning these, you should include a glossary at the end where others can read up on the exact definitions of the technical terms.
Automate the process if you can
If you stick to the end, we’ll show you how.
To give you a quick spoiler: there are certain dedicated digital forensics solutions such as SalvationDATA’s Digital Forensic Lab that take out the heavy lifting of having to write a digital forensics report on your own, with a built-in chain of custody compliance, timestamps, etc.

Studying a computer forensic evidence report example written by others will not only get your creative juices flowing, let you in on some ideas about what to include in your report, but give you a good overall image of what the finalized version is supposed to look like.
Below, please find our digital forensic report template list consisting of top-performing industry examples.
- A shorter report outlining the case of document manipulation (by Cybersleuthlab)
- A detailed digital forensics report featuring tables, exhibits, figures, etc.
- A report explaining video footage with timestamps

Now comes the most important step of all – actually writing the digital forensics report .
Since you’re now familiar with the best practices of how to approach the task, we can move on to the exact structural specifics of it.
Please include the name of the case, the investigator in charge, and the relevant dates.
b) Table of contents
Just like a book, your digital forensic report should list out every section and map out the corresponding page of the chapter.
If you’re using a popular text editor like Microsoft Word, this section can be auto-generated.
c) Case summary
This section should provide a general overview of the case.
Do not include too many details and try to avoid technical jargon if possible.
d) Evidence
The summary of the evidence submitted comes first. After that, you should list one after another and include screenshots if needed, besides, make sure to provide an explanation for each.
In this section, it’s fine to list any relevant hardware specifics such as the model name, serial numbers, etc.
e) Objectives
In essence, the objectives section should attempt to answer the question of what you’re trying to prove.
That being said, what was the objective of the investigation?
Don’t forget to include your hypothesis and any relevant search terms.
f) Steps taken during an investigation (aka. Forensic Analysis).
This section should outline the steps taken during the investigation, including the digital forensics methodology used and any interactable parts of the process.
You should also consider including additional explanations that extrapolate the process and give valuable insights into how crucial conclusions were made.
For the sake of readability and maintaining the chain of custody , you should also provide a timeline of events that specifies who handled the evidence, for how long, and for what purpose.
g) Tools used
What digital forensic tools did you rely on during the digital forensics investigation ? Outline them briefly and explain what purpose each of them served, including any limitations of said tools.
Attaching screenshots of the process and describing it can help make it sound clearer and more understandable to follow even for non-industry professionals involved in the case and/or legal procedure.
h) Relevant findings
Re-iterate the most important conclusions here and don’t be afraid to go into as many details as you see fit. Anything you state here should be directly related to the main objectives of the digital forensics investigation .
This is where you explain each piece of evidence and clearly pinpoint what it proves in a way that even non-industry professionals can understand.
i) Recommended next steps
This section should be short (no longer than a paragraph).
In it, suggest what the council can do with these findings and how to go from here.
Should criminal charges be filed?
j) Appendices (optional)
Not required, but it can make or break a case sometimes.
This is where you’ll be presenting your exhibit A, exhibit B, etc. You should present them in a PDF format that can be easily opened anywhere all while retaining its intended formatting.
Make sure that any hyperlinks it contains are clickable and that they link to relevant resources.
k) Formatting (optional)
This is mainly for the sake of the document having a professional appearance.
Having each page marked with a number also makes it easy to detect if someone tried to tamper with the report by removing a page (or if one of them accidentally goes missing).
Make sure the logo of your law enforcement organization is clearly visible in the header and footer of each page, as well as the corresponding address and the person in charge.
l) Figures (optional)
Your digital forensics report will likely contain various figures scattered throughout the document.
It’s nice to have a dedicated page where all of these can be reviewed in the same place.
Make sure there is a description alongside every figure stated.
m) Glossary (optional)
At some point when writing the report, there will be no other way than to mention some technical or industry-specific terms, although the best practice is to avoid them in general or at least keep them to a minimum.
Including a glossary at the end of the document will help non-industry professionals understand the complex terms mentioned in the report.
Make sure to include only those that you actually referenced during writing.

This is the part where you should re-check that everything is in order, and factually correct and that you haven’t forgotten to include anything (please refer to the sections above if you need further guidance).
As you refine the final version of the document, you should ask yourself:
- Do the numbers check out?
- Does the report list all crucial pieces of evidence and the people in charge?
- Is it brief and to the point or do you feel like you could trim out some irrelevant parts?
- Is it based on facts? If you catch yourself writing ‘I believe X’, perhaps it’s better to word it as ‘the evidence suggests that X happened because of Y’.
- Could certain sections be explained using layman’s terms instead of using complicated jargon?
Once everything checks out and you feel no further improvements can be made, you’re good to proceed to the final step!

Once you’ve double-checked everything, you can confidently present the report to the court.
If you’d like more detailed guidance, we’ve written a comprehensive guide on what steps are required to present evidence in court .
For your quick glance, please find a brief summary below:
- Secure the evidence.
- Make sure to maintain the chain of custody.
- Verify that the evidence is authentic.
- Sort the evidence according to its relevance.
- Convert the files into the right format.
- Get acquainted with the presentation procedure.
- Label the exhibits.
- Complete the final preparations.
It is our hope that the steps outlined above will take the hassle out of the equation and give you a solid idea of what the court expects to see.
Make sure to also familiarize yourself with the dos and don’ts of presenting evidence in court so that it will deem it admissible.
Most law enforcement professionals would agree that writing a digital forensics report is not the most productive part of the overall investigation. As necessary as it may be, it consumes a lot of man-hours that could be better spent analyzing evidence and taking a proactive role in the investigation.
To provide an alternative and do away with mindless manual labor, SalvationDATA has come up with a Digital Forensic Lab , a cutting-edge one-stop technological solution designed to streamline your digital forensics workflow and fully automate the reporting.
Thanks to its powerful architecture, evidence visualization, and built-in reporting, you will be able to close more cases in (even in advance )record time, thus adding to the credibility and recognition of your department, all while effortlessly maintaining the chain of custody and staying compliant with other industry requirements.
In the end, due to giving you such massive time and money savings, investments like these virtually pay for themselves.
Digital Forensic Lab completely automates the process of generating a forensic report.
At the end of the day, a digital forensics report is meant to facilitate communication between different industry experts that are involved in the case in one way or another. Some may have a background in IT, some are legal professionals, and some are officers of the law doing the fieldwork of collecting and securing crucial evidence.
With this in mind, the report doesn’t need to be perfect, nor does it need to include every single detail regarding the investigation. As long as you focus on the most important elements, use clear and concise language everyone can understand, as well as stick to the best practices we’ve outlined above, you should have a firm starting point on how to proceed.
Related posts
Essential guide to write blockers in digital forensics, 10 techniques for log file analysis in digital forensics, key benefits of disk imaging for data recovery, cloud forensics: how to collect and preserve evidence effectively, stellar photo recovery: compare features, pricing & performance, network forensics: investigating cyber attacks in real-time, md5 and sha1: essential hash values in digital forensics, key steps in malware analysis for digital forensics investigations, 3 steps to identify a mobile phone when disconnected., essential forensic imaging tools for digital investigations, professional solutions, digital forensic lab, video investigation portable 2.0, database forensic analysis system, smartphone forensic system professional, recent posts, photo vault recovery: restore lost or deleted files quickly, subscribe to our newsletter.
Home — Essay Samples — Law, Crime & Punishment — Forensic Science — Forensic Science Case Study
Forensic Science Case Study
- Categories: Forensic Science
About this sample

Words: 909 |
Published: Mar 19, 2024
Words: 909 | Pages: 2 | 5 min read
Table of contents
I. introduction, ii. background of the case study, iii. forensic techniques used in the case study, a. dna analysis, b. fingerprint analysis, c. ballistic analysis, challenges faced in the case study, v. conclusion, vi. recommendations, vii. future research, viii. references.

Cite this Essay
To export a reference to this article please select a referencing style below:
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Law, Crime & Punishment
+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
2 pages / 957 words
3 pages / 1424 words
3 pages / 1241 words
2 pages / 914 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Forensic Science
The use of hair evidence in criminal investigations has been a subject of controversy and debate for several decades. Hair evidence has been a crucial component in many criminal cases, often playing a significant role in the [...]
Hair testimony, a form of forensic evidence used in criminal investigations and trials, has long been a subject of scrutiny in the field of criminal justice. This essay delves into the complexities surrounding the validity and [...]
The trial of Christopher Cheary has sparked significant debate and controversy in the legal and psychological communities. Cheary was charged with the murder of three-year-old Sophia Acosta in 2011. The prosecution argued that [...]
'Capital Murder Law and Legal Definition.' USLegal.com, 2023, 2703.
In forensic science history, the importance of examining a hair or fiber was recorded at its early stages. One of the first forensic science articles involving the scientific study of hair was published in France, in 1857. This [...]
Forensic science, often referred to as the "silent witness" in the courtroom, plays a pivotal role in the criminal justice system. Its importance cannot be overstated, as it not only aids in solving crimes but also ensures that [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

7 Real-Life Cases Solved Using Digital Forensics [References]
Today, we will dive into the fascinating world of real-life cases that digital forensics technology has helped to crack open.
As you probably know, the power of digital forensics is immense and has revolutionized how we solve crimes.
So, buckle up and get ready for a thrilling journey through 7 real-life cases that digital forensics technology helped solve .
But first, let’s quickly remind ourselves of the various branches of digital forensics and who uses digital forensics in today’s world.
Digital forensics is vital for law enforcement, private investigators, and even corporations looking to protect their digital assets.
It’s incredible how this field has grown, and it’s only getting more important as technology evolves.
Case 1: The BTK Serial Killer
Get ready because we’re diving into one of American history’s most infamous criminal cases.
The BTK serial killer, also known as Dennis Rader, terrorized the people of Kansas for over three decades. But it wasn’t until digital forensics stepped in that the long, dark chapter in Kansas history finally came to a close.
Profiling the Killer
Between 1974 and 1991, Rader took the lives of ten innocent people, leaving behind a trail of fear and unsolved mysteries.
The killer got his nickname, “BTK,” from his chilling method of operation: Bind, Torture, Kill.
As the years went by, Rader managed to elude capture, taunting law enforcement with letters and clues, but never quite revealing his identity.
The Digital Breakthrough
Fast forward to 2004, when Rader made a fatal mistake. He sent a floppy disk to the police, believing it was untraceable. However, he was wrong.
Digital forensics experts were able to recover deleted data from the disk, which led them to a computer at a local church.
This critical piece of evidence allowed investigators to zero in on Rader, ultimately leading to his arrest and conviction.
The BTK case is a prime example of how digital forensics can help solve even the most long-standing mysteries.
And as technology continues to advance, it’s becoming increasingly essential for investigators to develop their digital forensics skills .
But that’s just the tip of the iceberg. Let’s move on to our next case, where digital forensics played a crucial role in bringing terrorists to justice.
Case 2: The Boston Marathon Bombing
On April 15, 2013, a day that should have been filled with joy and celebration, tragedy struck the city of Boston.
Two homemade bombs detonated near the finish line of the Boston Marathon, killing three people and injuring hundreds more.
It was a day that would forever be etched in the memories of those affected, but digital forensics would soon play a pivotal role in bringing the perpetrators to justice.
The Tragic Event
The bombings were the work of two brothers, Tamerlan and Dzhokhar Tsarnaev.
In the days following the attack, law enforcement launched a massive manhunt to capture the suspects, using every resource available to them.
This is where digital forensics would prove to be an invaluable tool in their quest for justice.
Analyzing Digital Evidence
Investigators turned to the vast amount of digital evidence available to help them identify the suspects.
Surveillance footage, cellphone data, and social media activity were all analyzed using advanced digital forensics techniques.
This allowed them to piece together the Tsarnaev brothers’ movements before, during, and after the attack.
But it wasn’t just traditional digital forensics at work here. Cloud forensics and mobile forensics also played a significant role in the investigation, as experts scoured the suspects’ online activities and cellphone records for vital clues.
Ultimately, digital forensics helped investigators to apprehend Dzhokhar Tsarnaev, who was later convicted and sentenced to death. His brother, Tamerlan, was killed during a police shootout.
The Boston Marathon bombing case is a powerful reminder of the importance of digital forensics in modern criminal investigations.
Now, let’s explore a case where digital forensics was used to unmask a deceptive online predator.
Case 3: Catching the Catfish
The internet can be a fantastic place to connect with people worldwide, but it can also be a breeding ground for deception and malicious intent.
In this case, we’ll explore how digital forensics was used to catch a “catfish” who had been fooling people into believing he was someone else entirely.
The Deceptive Online Relationship
A woman named Sarah met a man named “Chris” online and quickly fell for his charming persona. They exchanged messages and photos and even spoke on the phone.
But as their relationship progressed, Sarah started to feel that something wasn’t quite right. She decided to hire a private investigator, who soon discovered that “Chris” was not who he claimed to be.
He was, in fact, a catfish who created fake online profiles to deceive others.
Uncovering the Truth Through Digital Forensics
Digital forensics played a crucial role in exposing the catfish’s true identity. The private investigator used various digital forensics tools and software to analyze the images and messages sent by “Chris.”
By examining the EXIF metadata of the photos, the investigator was able to determine that they had been manipulated, and the phone number “Chris” had been using was linked to several other catfishing schemes.
Additionally, the investigator was able to trace the catfish’s online activities back to his real identity by analyzing his IP address and other digital footprints.
In the end, the catfish is confronted and forced to admit his deception, allowing Sarah to move on with her life.
This case is a prime example of how digital forensics can be used to solve serious crimes and help everyday people protect themselves from online deception.
Now, let’s take a look at a high-profile murder case where digital evidence played a critical role in the trial.
Case 4: The Murder of Laci Peterson
In 2002, the disappearance of Laci Peterson, a pregnant woman from Modesto, California, captured the nation’s attention.
The case took several twists and turns, but ultimately, digital forensics helped build a case against her husband, Scott Peterson.
The Disappearance
Laci was reported missing on Christmas Eve, and her husband, Scott, quickly became the prime suspect.
As the investigation unfolded, evidence began to mount against him, including suspicious behavior and extramarital affairs. But it was the digital evidence that would prove crucial in the courtroom.
The Role of Digital Evidence in the Trial
Investigators used digital forensics to analyze Scott’s computer, cellphone records, and GPS data, which painted a damning picture of his movements and activities before and after Laci’s disappearance.
For example, they discovered that Scott had researched fishing locations and currents in the San Francisco Bay, where Laci’s body was eventually found.
Another critical piece of digital evidence came from forensic imaging .
Experts created a detailed digital reconstruction of the crime scene, which helped the jury visualize and understand the complex timeline of events leading up to Laci’s murder.
In the end, Scott Peterson was convicted of first-degree murder for the death of his wife, Laci, and second-degree murder for the death of their unborn son.
He was sentenced to death, but his sentence has since been overturned, and he is currently awaiting a new trial.
The Laci Peterson case highlights the power of digital forensics in providing key evidence that can sway a jury and ensure that justice is served.
Let’s move on to another case that has captured the world’s attention for over a decade.
Case 5: The Disappearance of Madeleine McCann
In 2007, the world was shocked by the disappearance of three-year-old Madeleine McCann from her family’s holiday apartment in Praia da Luz, Portugal.
Despite countless leads and extensive investigations, Madeleine has never been found. However, digital forensics has played an essential role in the ongoing search for answers.
A Long-Running Mystery
Over the years, the case has generated numerous theories and suspects but no definitive answers.
As time has passed, the role of digital forensics in the investigation has become increasingly important, with experts analyzing vast amounts of data to find any clue that might lead to a breakthrough.
Digital Forensics: A Ray of Hope
One such instance where digital forensics played a crucial role in the Madeleine McCann case was when investigators analyzed the computers of a key suspect.
They discovered that the suspect had searched for information about the disposal of bodies and the effects of certain drugs on children.
This information and other evidence led to the suspect being named as a prime person of interest in Madeleine’s disappearance.
Additionally, digital forensics experts have examined countless images and videos from the area where Madeleine vanished, using data recovery techniques to recover and analyze deleted or damaged files.
They’ve also utilized database forensics tools to search through massive amounts of data in an attempt to find any potential leads.
While Madeleine McCann’s case remains unsolved, the tireless work of digital forensics experts continues to offer hope that one day, the truth will be uncovered, and justice will be served.
Now, let’s explore a case where digital forensics brought down a notorious online criminal empire.
Case 6: The Takedown of Silk Road
The Silk Road was once the most infamous online black market, a hidden corner of the internet where users could buy and sell drugs, weapons, and other illegal goods.
But in 2013, a daring operation led by the FBI brought the entire operation crashing down, thanks in large part to digital forensics.
The Rise and Fall of an Online Empire
Founded by Ross Ulbricht in 2011, Silk Road quickly gained notoriety as the go-to place for illegal transactions.
As the site grew, so did the attention of law enforcement agencies, who were determined to bring the operation to an end.
Digital Forensics to the Rescue
To build their case against Ulbricht, the FBI used advanced digital forensics techniques to trace the flow of money and communications through the anonymous network that Silk Road operated on.
This involved the use of file carving tools and other specialized software to analyze encrypted data and reveal the hidden connections between users and transactions.
By following the digital breadcrumbs, investigators were able to link Ulbricht to the Silk Road operation and eventually track him down in a public library in San Francisco, where he was arrested.
Ulbricht was later convicted of multiple charges, including money laundering, computer hacking, and drug trafficking. He was sentenced to life in prison without parole.
The Silk Road takedown is a prime example of how digital forensics can help law enforcement dismantle criminal networks operating in the shadows of the internet.
Now, let’s move on to our final case, where digital forensics played a key role in solving a heartbreaking murder mystery.
Case 7: The Murder of April Jones
In 2012, the small town of Machynlleth, Wales, was rocked by the abduction and murder of five-year-old April Jones.
The case quickly gained national attention, and the desperate search for April captured the hearts of millions. Once again, digital forensics would prove to be instrumental in securing a conviction.
A Town’s Worst Nightmare
April was last seen playing outside her home before being abducted by Mark Bridger, a local man with a history of violence.
Despite a massive search effort involving hundreds of volunteers, April’s body was never found. But the evidence against Bridger continued to mount.
Digital Forensics at Work
In the days following April’s disappearance, investigators turned to digital forensics to build their case against Bridger.
They discovered that he had attempted to destroy evidence by deleting files and wiping his computer’s hard drive.
But digital forensics experts were able to recover critical data, including images of April and internet searches related to child abduction and murder.
Digital forensics also played a role in linking Bridger’s vehicle to the crime scene. By analyzing GPS data from his car, investigators were able to place him at the scene of April’s abduction and track his movements afterward.
The recovered digital evidence helped secure Bridger’s conviction for April’s murder, and he was sentenced to life in prison.
The April Jones case is a tragic reminder of the importance of digital forensics in the pursuit of justice. It demonstrates how even the most determined criminals can be brought to justice through the diligent work of digital forensics experts.
These seven real-life cases offer a glimpse into the remarkable power of digital forensics in solving crimes and bringing criminals to justice.
As technology continues to evolve, so too will the methods and techniques used by digital forensics experts, ensuring that they remain a vital tool in the fight against crime.
References Used
Here are the references for each of the seven cases discussed in the blog post:
- Ramsland, K. (2006). Inside the Minds of Sexual Predators. Greenwood Publishing Group.
- Douglas, J. E., & Dodd, J. (2007). Inside the Mind of BTK: The True Story Behind the Thirty-Year Hunt for the Notorious Wichita Serial Killer. John Wiley & Sons.
- NPR (2015). What We Know About The Boston Marathon Bombings, 2 Years Later. Retrieved from https://www.npr.org/sections/thetwo-way/2015/04/15/399751623/what-we-know-about-the-boston-marathon-bombings-2-years-later
- CBS News (2019). Boston Marathon bombing timeline of events. Retrieved from https://www.cbsnews.com/news/boston-marathon-bombing-timeline-of-events/
- The Guardian (2013). The perfect man who wasn’t: when the man you love is a conman. Retrieved from https://www.theguardian.com/lifeandstyle/2013/nov/23/the-perfect-man-who-wasnt
- Crier, C. (2005). A Deadly Game: The Untold Story of the Scott Peterson Investigation. Harper Collins.
- CNN (2004). Peterson jury sees pictures of Laci’s remains. Retrieved from https://edition.cnn.com/2004/LAW/09/29/peterson.trial/index.html
- The Telegraph (2021). Madeleine McCann: The key events in the search for the missing girl. Retrieved from https://www.telegraph.co.uk/news/0/madeleine-mccann-key-events-search-missing-girl/
- BBC News (2020). Madeleine McCann: Suspect investigated over other missing girls. Retrieved from https://www.bbc.com/news/uk-53044605
- Greenberg, A. (2015). The Untold Story of Silk Road, Part 1. Wired. Retrieved from https://www.wired.com/2015/04/silk-road-1/
- U.S. Department of Justice (2015). Ross Ulbricht, the Creator and Owner of the “Silk Road” Website, Found Guilty in Manhattan Federal Court on All Counts. Retrieved from https://www.justice.gov/usao-sdny/pr/ross-ulbricht-creator-and-owner-silk-road-website-found-guilty-manhattan-federal-court
- BBC News (2013). April Jones: The schoolgirl who disappeared from her street. Retrieved from https://www.bbc.com/news/uk-wales-24384394
- The Guardian (2013). Mark Bridger found guilty of abducting and murdering April Jones. Retrieved from https://www.theguardian.com/uk/2013/may/30/mark-bridger-guilty-april-jones

Related Posts

Does Digital Forensics Require Coding or Programming Skills?
A career as a digital forensics analyst sounds exciting, especially when it involves uncovering digital evidence, helping to apprehend suspects, and testifying in a court…

Who Benefits From Using Digital Forensics: 5 Types of People
Digital forensics is an important field that involves recovering, analyzing, and preserving digital evidence from electronic devices. It can be used to investigate cybercrimes, data…

The 9 Different Branches Of Digital Forensics [Explained]
Digital forensics is crucial in investigating and prosecuting cybercrime, fraud, and other illegal activities. As technology advances, the need for specialized digital forensics expertise becomes…

How Long Is Chat History Saved In WhatsApp? [Explained]
If you use WhatsApp frequently, you may be wondering how long the app keeps your chat history. WhatsApp is a popular messaging app that is…

A Comprehensive Guide to Digital Forensics [Tools & Career]
Hey there! If you’ve ever wondered, “What is digital forensics in simple terms?” you’ve come to the right place. Digital forensics is the process of…

VPN Comparision Between Private Internet Access vs.Hide.ME
Hey there, fellow VPN enthusiasts! You might be wondering, “Is Hide.Me a legit VPN?” or even, “Is there a better VPN than PIA?” Well, you’re…

13 Benefits of Using Telegram App for Business [Guide]
Hey there! Are you wondering why Telegram is good for business? Look no further! In today’s fast-paced world, businesses are always on the lookout for…

Does Telegram Show Your Location? [App Settings & Sharing]
Telegram is an increasingly popular messaging app that’s been gaining traction for its focus on privacy and security. Unsurprisingly, many people wonder, “Does Telegram show…
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Search This Blog
Chemistry and biochemistry academy.
Chemistry and Biochemistry Academy(CAB) is a platform for learners. If you have anything to share with us then do not hesitate to contact CAB through [email protected].
How to write a Forensic Case Study: Murder of Junko Furuta

They will pay more than what they did to her.

They and their generations will pay for what they did to this young lady.

This post is a great resource for so many blog things. Thanks for the info. to get buy medicine online from Dose Pharmacy

penegra 100mg is perceived as one of the most incredible FDA-supported ED pills. Because of its promising outcomes, it is turning out to be progressively famous. This erectile dysfunction (ED) or male weakness pill brags enduring adequacy for close to 5 hours and you’ll feel so satisfied with your sex drive. Trust us; if you’re searching for an outcome situated ED pill, this regular method for get stronger erections is all you want at present!
Waklert 150 | Armodafinil | Best Narcolepsy Savvy Tablets. purchase waklert 150 online to advance attentiveness in the psyche. It is endorsed for unnecessary drowsiness brought about by obstructiv..
Vilafinil 200 is a brand of conventional Modafinil that you can use for relieving rest problems. This is a pill that can assist you with staying conscious. Its essential use is for restoring patients of rest problems, for example, narcolepsy which is a remarkable issue in itself that doesn't permit you to create
Modvigil 200 is a nootropic delegate of adrenergic specialists ( focal sensory system energizers) that advances attentiveness and is useful for people who have extreme sle.
What Is Modalert 200 ? Modalert is a neuro-upgrading (eugeroic) drug opiate got to act toward a lack of fixation and different rest diseases which incorporates...
Cenforce 120mg Tablet (Sildenafil) Fildena 100 Mg Vidalista Dark 80 Mg Fildena 150 Mg Cenforce 150 Mg Cenforce 100mg tablet fildena double 200
Post a Comment
Popular posts from this blog, roles of sodium carbonate when extracting caffeine from tea leaves.

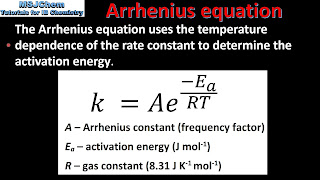
Arrhenius equation: Increasing temperature increases the rate reaction
🎧 STREAM ON ALL PLATFORMS
Top 10 true crime cases solved thanks to forensic science

Discover forensic science has brought resolution to some of the most frustrating cold cases in true crime history.
New scientific discoveries are made every single day. And in the world of true crime, forensic science is one of the strongest investigative tools at law enforcement’s disposal. Few things are as satisfying as solving a haunting cold case with new technology, finally bringing closure to victims’ loved ones.
Join us as we look at the top 10 cold cases that were once shrouded in mystery but have since been solved, thanks to the relentless pursuit of truth and the power of cutting-edge forensic techniques.
1. The Tragic Abduction of Jacob Wetterling
The journey begins with the heartbreaking abduction of 11-year-old, Minnesota kid, Jacob Wetterling in 1989. This case remained unsolved for 27 agonising years until advances in DNA analysis led to the apprehension of the culprit, Danny Heinrich. The breakthrough came when suspected child molester Heinrich's DNA was linked to the crime scene, providing long-awaited answers for the Wetterling family.
2. The Murder of Hae Min Lee: Adnan Syed's Conviction Overturned
The gripping case of Hae Min Lee's murder and Adnan Syed's conviction became a sensation through the podcast "Serial." After years of legal battles, advances in genetic profiling helped overturn Adnan Syed's conviction. Tests were performed on Hae Min Lee's clothes, including a pair of her shoes, contained a DNA sample – excluding Adnan Syed. However, in March 2023 his conviction was reinstated and the possibility of him returning to prison has sparked serious debate.
3. The Claremont Serial Killer
The Claremont Serial Killer case in Western Australia involved the murders of three young women in the 1990s. It remained unsolved for over two decades. In 2020, Bradley Robert Edwards was convicted of the murders due to advancements in forensic DNA analysis, which allowed authorities to match his DNA to samples found at the crime scenes.
4. The Golden State Killer
The Golden State Killer terrorized California for over a decade, committing a string of burglaries, rapes, and murders. The case went cold for years until the perpetrator, Joseph DeAngelo, was apprehended in 2018. Forensic genealogy and DNA analysis played a pivotal role in identifying and capturing him, providing closure to the victims' families and the communities he haunted.
5. The Identity of “Little Miss Nobody”
For nearly six decades, the identity of “Little Miss Nobody,” a young girl found murdered in Arizona in 1960, remained a mystery. In 202, forensic genealogy and DNA analysis enabled authorities to identify her as Sharon Lee Gallegos, opening up new avenues for solving this decades-old cold case. Sharon was four years old when she was abducted outside her New Mexico home, and her kidnapper has not been caught.
6. The Yorkshire Ripper
The Yorkshire Ripper, Peter Sutcliffe, terrorized northern England from 1975 to 1980. Despite an extensive manhunt, he evaded capture until 1981, when he was arrested for a minor offense. Advanced forensic techniques, particularly fibre analysis and blood typing, helped link him to the murders, resulting in his conviction for the brutal slayings of 13 women.
7. The Tokyo Sarin Gas Attack
The Tokyo Sarin Gas Attack in 1995 was a shocking act of terrorism orchestrated by the Aum Shinrikyo cult. The attack killed 13 people and more than 5,500 people sustained injuries. Forensic science played a crucial role in identifying the nerve gas used to linking it to the cult members. This led to the arrest and conviction of the individuals responsible for the attack. [
8. The Boy in the Box: America's Unknown Child
The heartbreaking case of America's Unknown Child, found deceased in a cardboard box in 1957, has baffled investigators for over six decades. In recent years, renewed forensic efforts and genetic genealogy have made it possible to finally identity the boy as 4-year-old Joseph Augustus Zarelli. Joseph came from a prominent Delware County, Pennsylvania family, yet his body showed signs of malnutrition, bruising and scarring. The investigation into his death continues.
9. The Alcasser Girls Case
The disappearance and murder of three teenage girls in Alcasser , Spain, in 1992, was a case that deeply shocked the nation. After years of uncertainty, advancements in forensic science, including DNA analysis led police to the door of Antonio Anglés in 2019. Anglés had been one of the prime suspects in the investigation and investigators were elated when his guilt was proven.
10. The Disappearance of Bobby Dunbar
In 1912, four-year-old Bobby Dunbar disappeared during a family vacation in Lousiana. After an extensive search, a boy believed to be Bobby was found and reunited with his family. However, Julia Anderson claimed the boy was her son, Bruce. In 2004, almost a century later, DNA testing revealed that the boy was indeed not Bobby, leading to reopening the case.
Further Reading:
Jacob Wetterling
Timeline: The Adnan Syed Case
Little Miss Nobody identified
Who is the Claremont Serial Killer?
Tokyo Subway Attack
Suspect in 1972 Cold Case died by suicide before he was convicted
Love True Crime? Subscribe to Evidence Locker Podcast in Apple Podcasts , or wherever you listen to podcasts and join us as we uncover the chilling tales of true crime.
Related Posts

The Menendez Brothers: A Social Media Renaissance and What It Means for True Crime
The Menendez brothers' case has gained renewed attention on social media, as a new generation revisits their 1990s conviction through the le...

Shadows on the Freeway: The Dark Legacy of California's Killers
In 1970s California, highways symbolized freedom but hid a dark secret. Killers like Patrick Kearney and William Bonin preyed on young men, ...

Evidence Locker’s Top 10 Most Listened-To Episodes Ever: Dive Into the World’s Most Gripping True Crime Cases
Discover the top 10 most listened-to episodes of Evidence Locker, where we explore the world’s most chilling true crime cases. From notoriou...

220: Killer Butcher, Katherine Knight | Australia

It seems we can’t find what you’re looking for. Perhaps searching can help.
We use cookies to enhance our website for you. Proceed if you agree to this policy or learn more about it.
- Essay Database >
- Essays Samples >
- Essay Types >
- Case Study Example
Forensic Evidence Case Studies Samples For Students
5 samples of this type
WowEssays.com paper writer service proudly presents to you an open-access catalog of Forensic Evidence Case Studies meant to help struggling students tackle their writing challenges. In a practical sense, each Forensic Evidence Case Study sample presented here may be a guidebook that walks you through the important phases of the writing procedure and showcases how to compose an academic work that hits the mark. Besides, if you require more visionary help, these examples could give you a nudge toward an original Forensic Evidence Case Study topic or encourage a novice approach to a threadbare issue.
In case this is not enough to slake the thirst for effective writing help, you can request personalized assistance in the form of a model Case Study on Forensic Evidence crafted by a pro writer from scratch and tailored to your particular requirements. Be it a simple 2-page paper or a sophisticated, lengthy piece, our writers specialized in Forensic Evidence and related topics will submit it within the stated period. Buy cheap essays or research papers now!
Assuming That Legal Authority Was Not An Issue, Should Vpd Personnel Or A Multijurisdictional Case Study
Example of case study about jeffrey dahmer, computer forensics: free sample case study to follow.
Don't waste your time searching for a sample.
Get your case study done by professional writers!
Just from $10/page
Case Study On Cyber Security 1 PT 1
Proposing a digital forensics grange security case study examples.
Password recovery email has been sent to [email protected]
Use your new password to log in
You are not register!
By clicking Register, you agree to our Terms of Service and that you have read our Privacy Policy .
Now you can download documents directly to your device!
Check your email! An email with your password has already been sent to you! Now you can download documents directly to your device.
or Use the QR code to Save this Paper to Your Phone
The sample is NOT original!
Short on a deadline?
Don't waste time. Get help with 11% off using code - GETWOWED
No, thanks! I'm fine with missing my deadline

IMAGES
VIDEO
COMMENTS
HOSA Forensic Science Sample Case Study 2019 EXTERNAL EXAMINATION: 6/26/2013, 1005 hours. The body is that of an unembalmed adult male who appears the stated age of 20 years. The body is identified by toe tags. The body weighs 110 pounds, measures 67 inches in length and is lean and fairly well nourished.
Case Studies & Stories. 10 Famous Cases Cracked by Forensics. October 31, 2014. 1. 175333. Share. Facebook. ... key testimony from handwriting analysts matched his writing to that on the ransom notes. Additional forensic research connected the wood in Hauptmann's attic to the wood used in the make-shift ladder that the kidnappers built to ...
Here we present a complex forensic case regarding a double murder whose victims were found almost completely skeletonized. Post-mortem investigations allowed us to define the biological profile of the two bodies (ancestry, sex, age and stature), to discover their identity through forensic DNA analysis, and to detect peri-mortem injuries caused ...
STEP 1: Familiarize Yourself with the Best Practices of Writing a Digital Forensic Report; STEP 2: Study Some Generic and Recommended Forensic Report Examples before Writing; STEP 3: Write the Digital Forensics Report; STEP 4: Re-check Your Report for Factual Correctness and Apply Edits as Needed; STEP 5: Present the Report to the Court
In conclusion, the case study exemplifies the critical role that forensic science plays in solving crimes and delivering justice. Through the use of advanced forensic techniques such as DNA analysis, fingerprint analysis, and ballistic analysis, investigators were able to unravel the complex web of evidence and identify the true perpetrators of ...
Case 4: The Murder of Laci Peterson. In 2002, the disappearance of Laci Peterson, a pregnant woman from Modesto, California, captured the nation's attention. The case took several twists and turns, but ultimately, digital forensics helped build a case against her husband, Scott Peterson. The Disappearance
For one to score high marks in a Forensic Case Study, one must adhere to the following: Background of the case: This section contains details about the crime. It includes; the reasons for committing the offense, the conditions which the crime was committed, the circumstances of the crime scene and clear identification of the suspect(s) and the ...
Few things are as satisfying as solving a haunting cold case with new technology, finally bringing closure to victims' loved ones. Join us as we look at the top 10 cold cases that were once shrouded in mystery but have since been solved, thanks to the relentless pursuit of truth and the power of cutting-edge forensic techniques. 1.
Recent Posts. Case Study: How Forensic Video Analysis Helped Solve a Complex Crime December 2, 2024; The Digital Forensic Expert's Playbook: Best Practices and Strategies November 29, 2024; The Dark Web's Digital Trail: A Computer Forensics Perspective November 27, 2024; Hacking the Hackers: How Cyber Forensics Turns the Tables November 25, 2024; Why Video Enhancement Matters: The Impact ...
WowEssays.com paper writer service proudly presents to you an open-access catalog of Forensic Evidence Case Studies meant to help struggling students tackle their writing challenges. In a practical sense, each Forensic Evidence Case Study sample presented here may be a guidebook that walks you through the important phases of the writing procedure and showcases how to compose an academic work ...